- +917700986505
- G3/12 Jal Padma CHS Goregaon West Mumbai 400104
- [email protected]
You have spent lakhs / millions to enable information and cybersecurity in your organization, but everyone still tells you that you are at risk. How do you know what you did and what is being advised is going to cure you of your sleepless nights!
Risk is omnipresent and you need to constantly update your systems to manage it, and to manage all new threats. To do this you need effective and effectively designed processes.
Business Process Re-engineering is recognized as an effective tool to raise your business productivity and profitability through design changes.
The same rule holds true for your security management system. Remember that cybersecurity is a managed process which orchestrates the working of people and technologies. The security management process and outcomes result in organizational resilience through proactive, or reactive, security controls.
Our Security Re-engineering practice will assess the design and present state of effectiveness of security controls that have been enabled.
The assessment will cover:
People:Resource strength, internal and outsourced skills, effectiveness and quality of training and awareness, hiring / onboarding / off-boarding, monitoring, drills, cultural issues and any other issues which may pose a risk to the security setup.
Technology:Security technology solutions in operation, configuration, patching, backup, testing, and overall effectiveness and completeness of the technology stack vis a vis the business size and risk.
Process:We will review and analyze IT and critical business processes that will cause high impact to operations in event of the manifestation of a risk / threat scenario. Our team will carry out a process mapping, as needed, to map the organization topology and to identify weak touchpoints from the security perspective.
The most effective control in the Information Security Management System is human awareness and knowledge of risks and threats and how to control them.
This is easy to achieve, using awareness programs that are well designed and share the message to end users in a simple jargon-free language.
Once the message is delivered, it is important to monitor, track and assess the effectiveness of the awareness program by measuring the response of users (recipients who have participated in the sessions) to potential incidents.
Our Awareness programs are designed and delivered in the spirit of sharing knowledge and not to provide “training” which is the main reason why awareness programs fail.
We will provide you with Customized program which will include:
1. Requirements of your Information Policies and the compliance expectations from end users.
2. Risks / threats in your line of business.
3. Share cases of security incidents in similar business.
4. Good practices and common-sense actions that will help lower the risk.
5. Security Technology and Controls based training for the operations and functional team members.
6. Security awareness for senior management and Board members.
7. Awareness training for BCP/DR etc
Our end-to-end Awareness Program will provide you with an annual calendar of events / sessions based on ISO27001 or any other standard / framework. We can train your team members who can then take up the awareness sessions to ensure continuous development and management of the program.
The session can be delivered as in-person program or in virtual mode via our hosted LMS.
All it needs are some practical and simple actions –
A set of methods (all good practices) to safeguard email messages, communication channels and accounts from unauthorized access, malicious attacks, misuse, misrepresentation, spoofing or social engineering.
Criminals use email as a tool for spreading malware, spam, and phishing attacks. They may also use spoofed messages to trick recipients into sharing sensitive information, resulting in identity theft or monetary loss. Email is the most commonly used entry method into an organization, communicating infected attachments, phishing links etc.
Statistics demonstrate that in 90% or more attacks were launched via email.
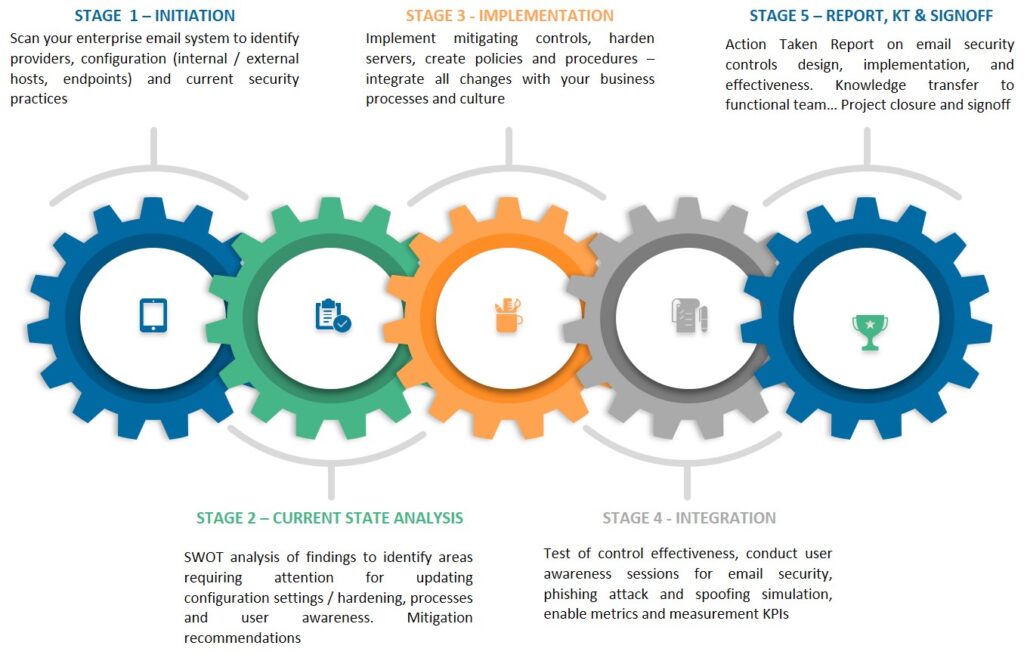
As the most widely used mode of communication in any organization, it is a critical need to ensure that the email system is secure and resilient to attack. Our guidance includes advice for:
1. Scanning and Configuration Mail Hosts.
2. Strong Authentication & Access Review.
3. Response, Monitoring, and Auditing.
4. Data Protection, Encryption and Leakage.
5. Network Analytics.
6. Protection from Business email compromise (BEC) threats.
7. System Level Controls DMARC, SPF, DKIM, BIMI
8. Email Attack Forensics.
9. Phishing Attack Simulation
We will integrate the best practices to safeguard your email systems by assisting to implement above mentioned guidance activities and controls.
Security in the cloud is much like security in your on-premises data centers – only without the costs of maintaining facilities and hardware. Many characteristics in the cloud such as enabling different policies and controls are the same as for any on-premise IT Architecture.
In the cloud, you don’t have to manage physical servers or storage devices instead, you use software-based security tools to monitor and protect the flow of information into and out of your cloud resources.
Cloud Security differs on different deployment models and the provider being used by the organization.
In cloud Security, one has to remember the considerations of the Shared Responsibility Model. This means that the Cloud Service Provider (CSP) is responsible for the security of the cloud infrastructure but you, the customer (or tenant, or user) are responsible for securing the data and applications that you put up in the Cloud.
Can you identify who will be responsible for each aspect of asset protection in the cloud environment, you as provider or as customer? We can help by providing the advisory and consulting inputs to set up the necessary and relevant processes. Or to obtain appropriate certification(s) that will help provide assurance to your stakeholders and interested parties. Mapping your processes and assets we can assist in identifying the touch points and the areas which need your oversight.
1. Cloud Testing – VAPT: Where required we will test your cloud infrastructure using Vulnerability Assessment and Penetration Testing (VAPT) methods that will help uncover technical weaknesses.
2. Cloud Security Training & Awareness: We will help provide training and awareness for your management and users with appropriate guidance on using the cloud services and how they can be responsible cyber cloud citizens.
3. Cloud BCP/DR: Being on the cloud does not translate into an assurance that your business is immune from disruption. Our BCP/DR services will provide the necessary inputs to build resilience into your cloud infrastructure.
4. Security Implementation: We help to ensure security of the complex cloud architecture enabled by your organization. This is achieved through the implementation of industry standards like ISO27017 and others, as well as regulatory practices such as PCI-DSS, or industry frameworks like CSA. We will help review, assess and measure your cloud and on-prem security practices, then plan your journey to a high level of maturity and assurance.
5. Cloud Infrastructure - Risk Assessment: We will help using risk and threat assessment practices supported by recommendations for remediation of the issues.
In today’s interconnected world, cybersecurity plays a pivotal role in protecting sensitive information and ensuring the integrity of digital systems. Open Security Alliance is committed to empowering organizations with cutting-edge security solutions that safeguard against evolving cyber threats. By fostering collaboration between cybersecurity experts and industry leaders, we help develop robust defense mechanisms that prevent data breaches, mitigate vulnerabilities, and enhance overall security posture.
we believe that security is a shared responsibility. Our platform promotes the exchange of knowledge, best practices, and innovative technologies to create a unified defense against cyber threats. By encouraging open communication and cooperation, we facilitate the development of standardized frameworks that address complex security challenges. This collaborative approach ensures that organizations of all sizes can adopt effective security strategies to protect their digital assets.
Innovation is at the heart of our mission at Open Security Alliance. We continuously explore emerging technologies such as artificial intelligence, machine learning, and blockchain to enhance cybersecurity capabilities. Our goal is to equip organizations with proactive tools that detect, prevent, and respond to cyber incidents efficiently. Through ongoing research and development, we strive to build a more resilient digital future where businesses and individuals can operate securely.
Compliance security is essential for organizations operating in regulated industries to safeguard sensitive data and adhere to industry standards. At Open Security Alliance, we provide comprehensive compliance solutions that help organizations meet regulatory requirements such as GDPR, HIPAA, PCI-DSS, and more. Our tailored compliance services ensure that businesses maintain data integrity, protect customer information, and avoid costly penalties by staying aligned with evolving security regulations.
we understand that compliance is not a one-time task but an ongoing commitment. Our compliance security services focus on implementing best practices, conducting regular audits, and ensuring continuous monitoring to maintain compliance standards. By fostering a culture of security awareness and regulatory adherence, we empower organizations to minimize risks, maintain trust, and protect their digital environments from potential threats.
To streamline the compliance process, Open Security Alliance leverages advanced technologies such as automated compliance monitoring, risk assessment tools, and real-time reporting systems. These solutions enable organizations to track compliance status efficiently and respond to any deviations swiftly. By integrating automation into compliance workflows, we help businesses reduce manual errors, improve operational efficiency, and maintain a strong security posture in an increasingly complex regulatory landscape.